Describe the Specific Vulnerability Metrics Used by Each Catalog
Common Vulnerability Scoring System CVSS rating is used as a guideline to identify and describe key metrics of a flaw and is meant to help customers prioritize the order. Each metric has a number assigned to each possible value AccessComplexity.
This attribute is useful for network devices and servers but rarely applies to software.
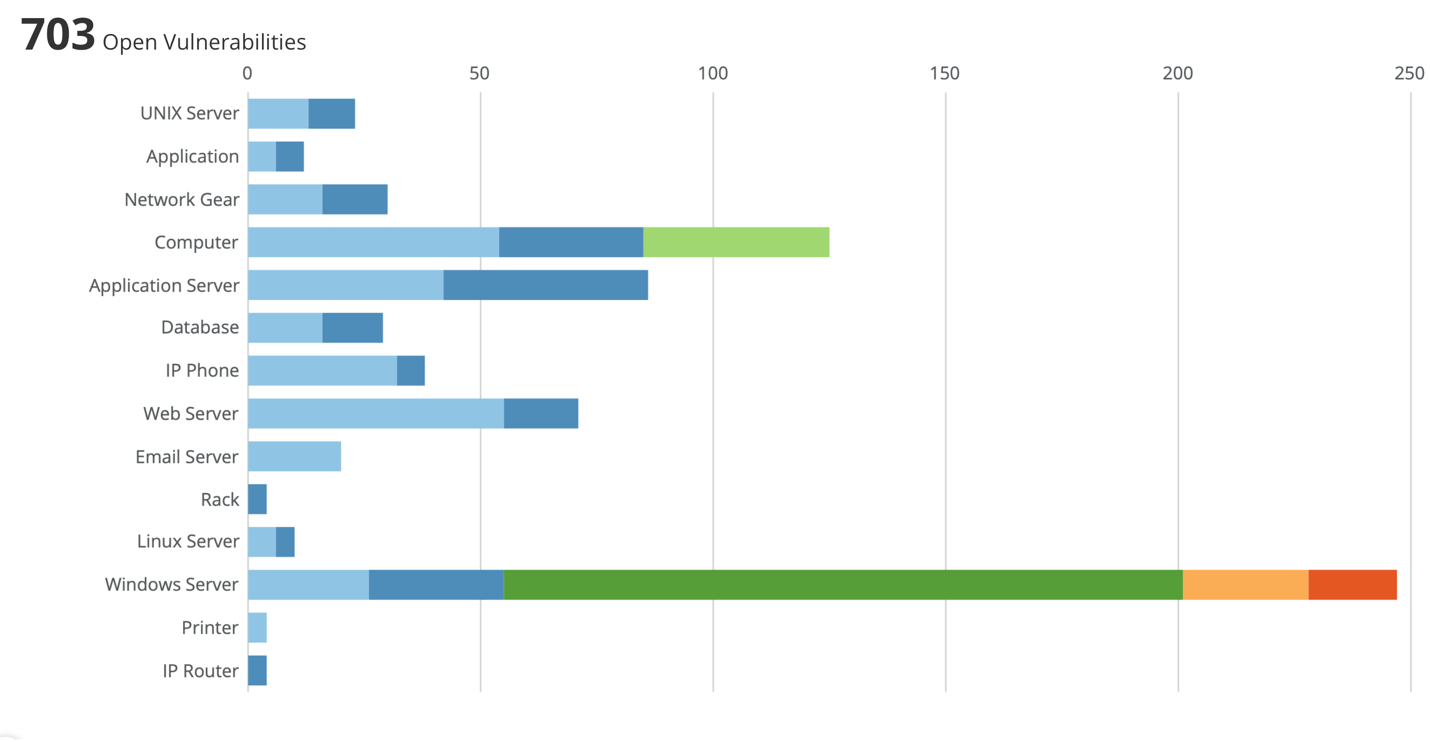
. B It is a centralized single pane of glass for all logs in a tenancy. The CVSS Score chart displays how many of your vulnerabilities fall into each of the CVSS score ranges. In the Executive Vulnerability Metrics dashboard there are 4 matrices that correlate vulnerabilities from the date the vulnerability is published to the time the vulnerability.
Common vulnerability scoring system CVSS This scoring system works to assign severity scores to each defined. High 035 medium 061 low 071 Integrity. Thats all for now.
In Part 2 we will. CVSS v30 Metric Groups. Cal Polys IT Security.
There are six base metrics that capture the most fundamental features of a vulnerability. In other words good metrics must be meaningful to specific organizational goals and key performance indicators. CPEs are used to describe what a CVE or CCE applies to.
Specific measurable attainable repeatable and time-dependent. None 00 partial 0275 complete 066. For vulnerability notes that cover more than one vulnerability eg.
To be truly useful metrics should also indicate the degree to which. Pouring through spreadsheets and creating. The three metrics in this group are.
Ad Leader in Vulnerability Risk Management Wave Report Q4 2019. Vulnerability scanning can be used at a broader level to ensure that campus information security practices are working correctly and are effective. These numbers can also be further broken down by department or system owner based on the requirements of each specific organization.
A vulnerability with at least one known working attack vector is classified as an exploitable vulnerability. 1 Access Vector AV. The CVSS score is calculated based on several metrics including exploitability attack.
Security teams today are constantly overwhelmed with the sheer quantity of potential vulnerabilities that they must mitigate. Temporal metrics change over time measuring a vulnerabilitys current state and the availability of patches. CVSS is composed of three metric groups Base Temporal and Environmental each consisting of a set of metrics as shown in Figure 1.
The risk level for each vulnerability Critical High Medium is governed by a specific score CVSS Score. Tuned to fit a specific organization or situation. Welcome to the modern era of cyber exposure.
The Common Vulnerability Scoring System CVSS is an open framework for communicating the characteristics and severity of software vulnerabilities. This score is based on access complexity required authentication and impact on data. Common Vulnerability Scoring System CVSS A universal way to convey vulnerability severity and help determine urgency and priority of responses A set of metrics and formulas Solves.
Effective metrics are often referred to as SMART ie. Describe the use of an IP address when deciding which attributes to track for each information asset. To use CVSS effectively it is important to calculate your own current and specific Temporal and Environmental metrics.
It measures how the vulnerability is exploited for instance locally or. A It can analyze critical diagnostic information that describes how resources are performing and being accessed. The window of vulnerability is the time from when the vulnerability.
Security analysts not only.
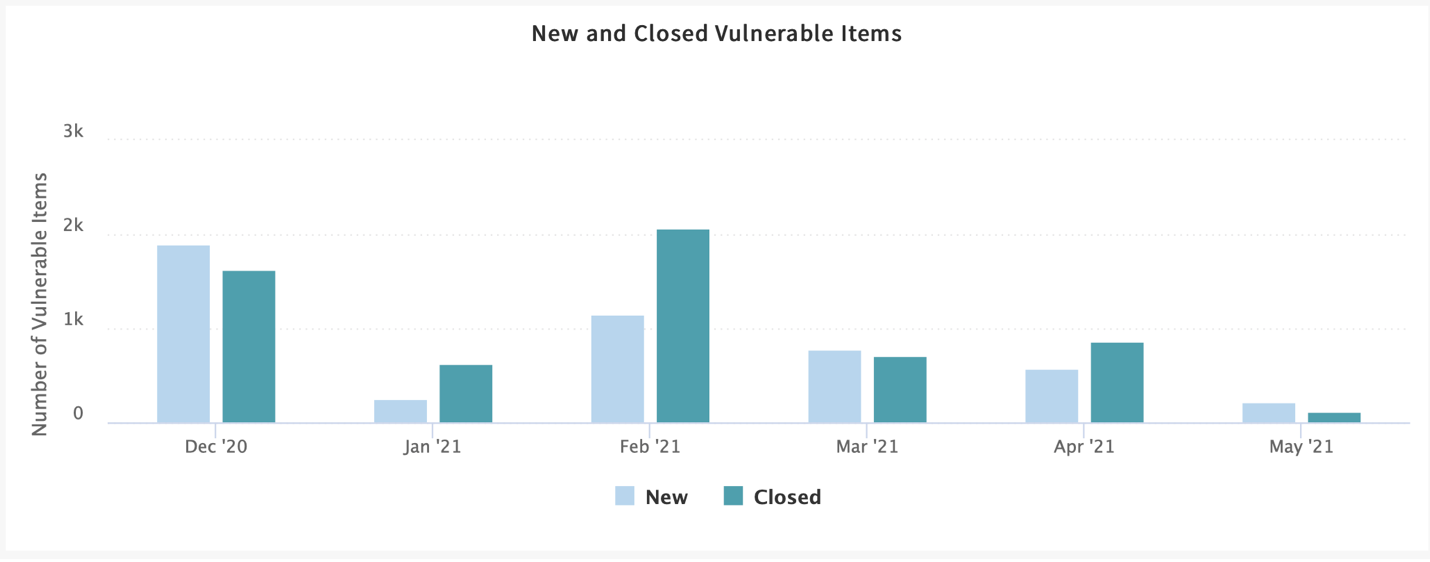
Vulnerability Management Metrics 5 Metrics To Start Measuring In Your Vulnerability Management Program Part 1 Of 2 Sans Institute Jonathan Risto

Vulnerability Management Metrics 5 Metrics To Start Measuring In Your Vulnerability Management Program Part 1 Of 2 Sans Institute Jonathan Risto
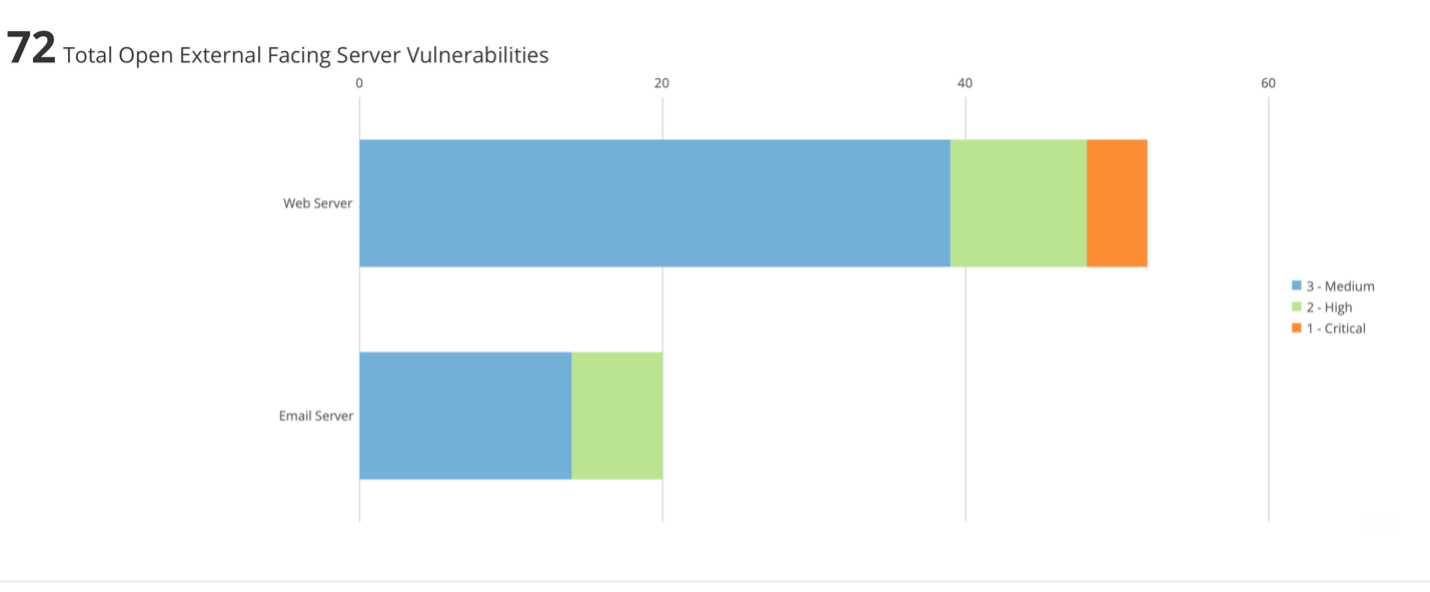
Vulnerability Management Metrics 5 Metrics To Start Measuring In Your Vulnerability Management Program Part 1 Of 2 Sans Institute Jonathan Risto
Comments
Post a Comment